Protect your environment without breaking the bank.
1CyberOps will help protect organizations of all sizes, including residential homes from cyber criminals.
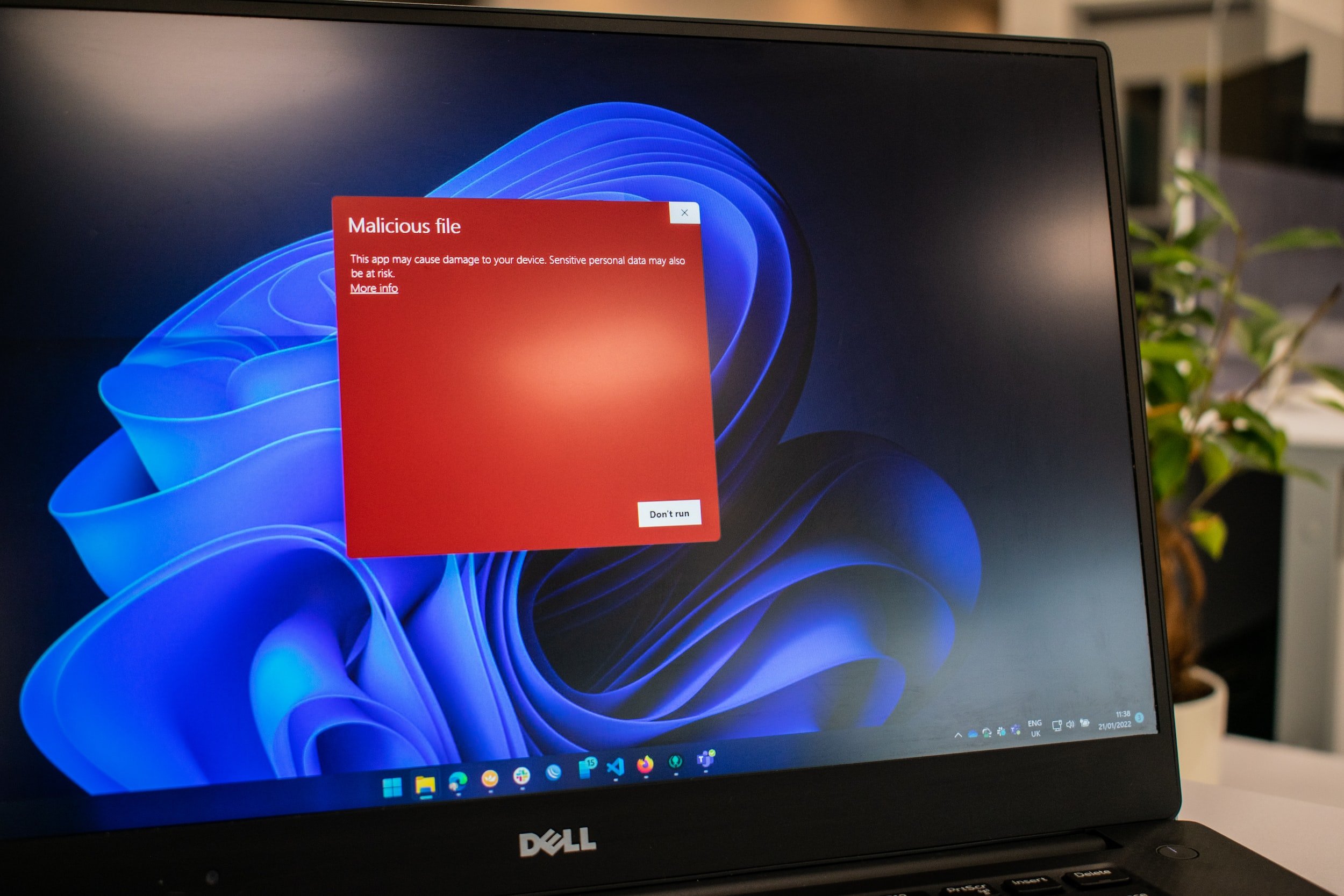
Endpoint Detection and Response (EDR)
The majority of breaches originate from endpoints, and with the shortage of cyber security professionals, organizations are pressed for time to remediate malware that is spreading through the environment.
1CyberOps solution will effectively identify threats and response with an action to stop further activity.
1CyberOps EDR solution will block brute force attacks, Zero-Day exploits, proactively hunting for unknown malware.
72-hour Ransomware rollback, along with conducting a forensic analysis.
Protect your end users within your organization, working from home, or from any location around the world.
1CyberOps can provide your security team with a guide for easy deployment instructions, training, and management console to monitor your endpoints.
Automated Incident Response (AIR)
The need for a speedy response to a cyber incident is inevitable. 1CyberOps approaches incidents with an automated incident response tool that will eliminate the manual efforts of your security analysts.
This will allow your security analyst to focus on other initiatives for your organization.
Your existing solution shouldn’t only remediate active malware. Residual files from malware should be removed.
AIR can be deployed alongside your existing solution or be deployed when needed to help remove malicious software.
1CyberOps can manage this service or train your existing security team on managing and deploy AIR
Endpoint Protection (EP)
The ease of Malware as a service has given cyber criminals little to no experience to run ransomware campaigns against all types of organizations.
A multi-layered approach isn't the silver bullet.
1CyberOps can provide a unified solution that is strong enough to thwart advanced attacks.
Anomaly detection to identify and block Zero-Day exploits, use behavioral monitoring and machine learning to identify threats across the web, memory, applications, and files.
Timeline analysis of the malicious activity
If you don’t have a security team, no problem. 1CyberOps can help monitor your organization.
DNS Filtering (DF)
Verizon’s Data Breach Investigation Report 2022 Summary findings show that Ransomware attacks rose a total of 25%. This was partly due because end users fell victim to phishing attacks.
Block connections to malicious web servers attempting to deliver malware.
Restrict your end users from accessing website categories like gambling, social media, games, which may decrease productivity.
We’ll help you align your end users internet access with your acceptable use and code of conduct policy.
Vulnerability Assessment (VA)
Cyber threats are evolving and if you aren’t diligent in identifying vulnerabilities on your endpoints, you could become a victim of a cyber crime.
1CyberOps VA service will proactively scan systems to identify vulnerabilities that could be exploited on the operating system and 3rd party software.
It takes organizations an average of 60 days to remediate vulnerabilities.
Detect vulnerabilities as they are discovered and patch immediately cutting back on remediation time.